Nintendo Just Kind of Banned Gaming Tournaments
With little exception, having age-appropriate gaming tournaments is a good thing for a game (and [...]
Chrome Just Rolled Out New Ad Policies
Did you get a notice that Chrome just updated its ad policies when you opened [...]
Using Biometrics: Is It Really Better?
Some phones allow users to use their biometric data as 2FA, or as a password [...]
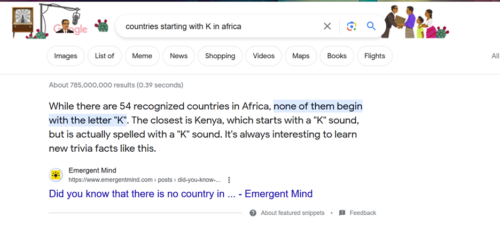
Fungus Guides Written By Bots – Don’t Die!!
The single biggest problem with AI right now is people abusing the shortcuts it presents. [...]
Degeneration of AI
ChatGPT has gotten worse at a number of things since its introduction to the public. [...]
Nov
What is a Browser Cookie?
A browser cookie is a little snippet of data that the browser stores while the [...]
How Does A Hacker Use Public WiFi?
Ads for VPNs give their two biggest benefits as often as they can: that you [...]
Google Monopoly: What Does It Mean?
Proving something or someone has a monopoly in today’s era of technology is difficult – [...]
Why Won’t My Bluetooth Devices Link Up?
1) How far away is your other item? Headphones, speakers, and keyboards generally aren’t going [...]
Unity Just Gut-Punched It’s Users For Profit
Unity is a game engine, and it’s famous for its versatility and low resource requirements. [...]