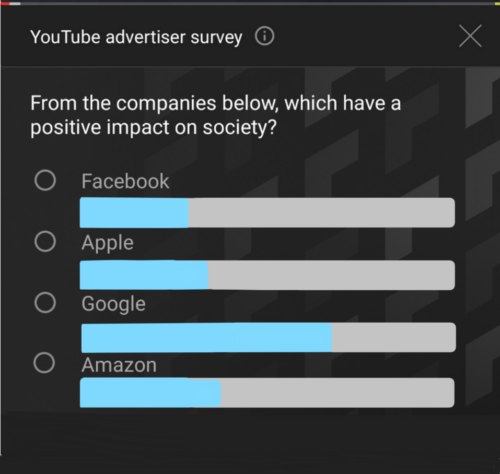
Online Survey Questions: How to do it Wrong
Experts have struggled with this problem for decades. How do you measure something subjective, and [...]
Oct
What’s a Kernel?
If your computer’s prone to bugs, you might have seen it give a ‘kernel error’ [...]
Oct
Captchas – How and Why
Captcha, which stands for Completely Automated Public Turing test to tell Computers and Humans Apart [...]
Smishing
Do you get strange solicitations for all sorts of things in your messages? Are you [...]
Streaming Services – and What Causes Failure?
Pinpointing success is much more difficult than pinpointing what causes a failure. Perhaps, if you [...]
Internet Hysteria: No, Your Fav isn’t Going to Die
Folks who were on Tumblr during its peak often see similarities in the content cycles [...]
Sep
Selling Scams : It’s Online Now, Too!
BetterHelp Betterhelp is notable because it’s one of a few online scams where the Youtubers [...]
Bad UI – Button Edition
Do you want to make a button that suuuuuucks? 1) Make Sure There’s no Context. [...]
Sep
REvil is Over Party
REvil, a notoriously tough ransomware, recently had a master decryptor released. What this means is [...]
Game Data is Getting Ridiculous
Why are game downloads so ridiculously huge? The first Doom game is famous for how [...]