General Remastering
Remastering just means changing the original quality of the master copy of a piece of [...]
What’s the deal with Google.amp links?
Google And Fast Loading If a mobile site takes even a second too long to [...]
Using Memes to Market? You Better do it Right
The era where anyone could make a meme and guarantee laughs is gone. Nowadays, marketing [...]
Internet Phenomenon to Boxer, Singer, Writer – Why Does it Keep Happening?
In General The world demands more out of its stars. In old media, [...]
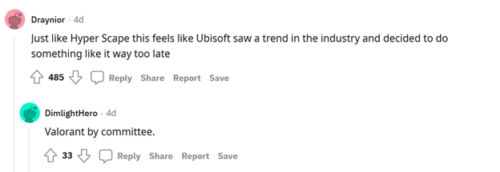
Tom Clancy’s XDefiant Already Looks Like a Mistake
Tom Clancy Does the name sound interesting? Does it ring a bell? Does it conjure [...]
Aug
Buzzfeed Unsolved ARG: Was that a Good Idea?
ARGs ARG stands for alternate reality game, and I’ve written articles on them before. [...]
Raid: Shadow Legends and Shotgun Marketing
How did this mobile game come to dominate every corner of advertising? The [...]
Small Sites Vs. A Big Internet
Art projects Some little art project websites deliberately avoid indexing their page, so it’s [...]
Why do Recipe Websites Give you an Essay Before the Recipe? Or, the ~Magic~ of Ads.
Cookbooks. They’re great. They don’t have to load their contents, and they usually contain [...]
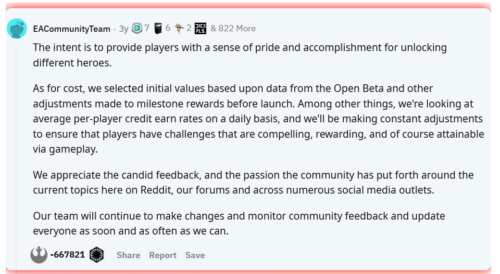
Gaming and Gambling: Microtransactions And Lootboxes
Gambling is widely considered an adult activity, and for good reason. It’s addictive, it has [...]
Jul