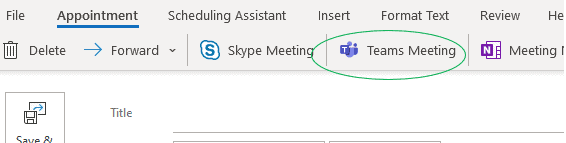
The US government has been forced to issue an alert to healthcare providers of a major new ransomware campaign that may impair their ability to treat COVID-19 patients.
The joint alert, issued by the FBI and Cybersecurity and Infrastructure Security Agency (CISA) and the Department of Health and Human Services (HHS), claimed that attackers using the Ryuk variant were targeting the sector with TrickBot malware.
Originally designed as a banking Trojan, TrickBot is now one of the most prolific pieces of malware around, offering a suite of functionality for various use cases including crypto-mining and POS data harvesting.
The alert warned of a relatively new Anchor_DNS module added by its authors which helps attackers use DNS tunnelling to keep C&C comms hidden and exfiltrate data seamlessly from high-profile targets. Anchor has already been used by North Korea’s Lazarus Group to steal data from victims.
The Ryuk variant has been around since 2018 and often threat actors deploy off-the-shelf tools such as Cobalt Strike and PowerShell Empire to steal credentials and maintain persistence. They also deploy “living off the land” techniques such as use of PowerShell, Windows Management Instrumentation (WMI), Windows Remote Management, and Remote Desktop Protocol (RDP) to move laterally, the CISA warned.
According to reports, an Eastern European cybercrime gang known as “Wizard Spider” is likely behind this latest campaign, which hit six hospitals in the same day including incidents in Oregon, New York and California. Some patients are apparently being forced to divert to other facilities as a result.
Mandiant CTO, Charles Carmakal, branded the gang, also known as UNC1878, “one of the most brazen, heartless, and disruptive threat actors” he’s ever seen.
“Ransomware attacks on our healthcare system may be the most dangerous cyber security threat we’ve ever seen in the United States. Patients may experience prolonged wait time to receive critical care,” he added.
“Multiple hospitals have already been significantly impacted by Ryuk ransomware and their networks have been taken offline. As hospital capacity becomes more strained by COVID-19, the danger posed by this actor will only increase.”
New data from SonicWall released today claimed that Ryuk now represents a third of all ransomware attacks so far this year, with detections soaring from around 5000 up to Q3 2019 to over 67 million over the past year.
The threat to healthcare is nothing new: Microsoft warned of an uptick in targeted APT-style ransomware attacks during the early days of the COVID-19 crisis.
We’re Elixis Technology
In the ever-changing, technology-centric world we live in, it’s vital to have an I.T. solution source you can count on. At Elixis Technology, it is our mission to help businesses — big and small — produce the results their customers demand, with technology that actually works.
.
News Source: https://www.infosecurity-magazine.com/